by admin
Wednesday, November 9th, 2016 at 11:21 am
A memory corruption in the Microsoft Windows Animation Manager which allows a malicious user to remotely execute arbitrary code on a vulnerable user’s machine, in the context of the current user. JavaScript POC ::HERE::
by admin
Tuesday, November 8th, 2016 at 3:20 pm

Bidirectional Unicode spoofing is not a new concept, malware has been using the technique for the last decade, but I was toying around with unicode earlier today for a phishing engagement, by default Win7 doesn’t allow you to create filenames with unicode chars unless you:
a. Open RegEdit
b. Navigate to HKey_Current_User/Control Panel/Input Method
c. Set REG_SZ “EnableHexNumpad” to be “1” (If there is no EnableHexNumpad, then add it and set its value to 1).
d. Reboot your system.
I didnt want to do this so I created a .vbs script that creates a .lnk file that spoofs the file extension with Unicode chars. This allows you to reverse the “.lnk” file extension, append “.txt” to the end and change the icon to notepad.exe’s icon to make it appear as a text file. When executed, the Target payload is a powershell webdl and execute.
This technique utlizes Right-to-Left Override [RLO] This trick uses the fact that some languages are being written from right side towards left. A Unicode character was created to support such languages. It displaces the displayed extension in reverse order ( i.e. blah.lnk becomes blahknl. ). This character code is: U+202e more information on this character ::here::. This doesn’t just apply to .lnk , you can do this trick with .exe, .com, .pif, .scr etc… files.
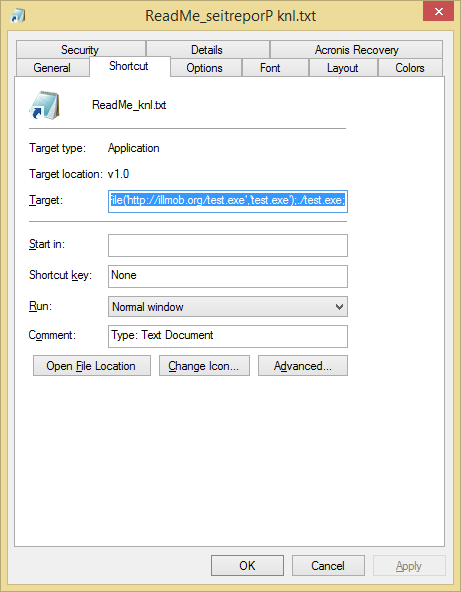
You can find the .vbs code on my GitHub ::here::
How-To: Download the .vbs file and edit the download url to point to your own payload. save the .vbs and execute it. The file named “ReadMe_knl.txt” will be created on your desktop. Send that to phishing target. May need to obfuscate further to bypass email security appliances.
To-Do: Make a script that allows you to choose whatever filename/extension you type and work on different payloads besides webdl.
BONUS: Created a PowerShell script to do the same thing that the vbs script does, although for some reason it hides the reversed ‘lnk’ from the filename
by admin
Tuesday, May 3rd, 2016 at 10:45 pm

☑ Nickname
☑ Logo
☑ Hype
☑ Website
☐ POC
https://imagetragick.com/
ImageMagick reported today (CVE-2016–3714) allows image uploads to trick the ImageMagick software into running commands instead, leading to a remote code execution(RCE)bug. More info ::HERE::
by admin
Thursday, April 14th, 2016 at 1:13 am
A new heap memory corruption (Out-of-Bounds Read) that affects Microsoft Office Excel 2007,2010,2013 and 2016. This vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Office Excel file (.xlsm).
Advisory & POC
by admin
Sunday, April 10th, 2016 at 3:44 pm
The build brings new changes targeting previously exploited dll-hijacking and uac bypass method vulnerabilities.
cliconfg.exe – can no longer be used as target for autoelevation as MS changed it manifest to autoelevate=false.
mmc.exe – event viewer console fixed, dll hijacking no longer works.
fake IIS inetmgr.exe launch from inetsrv appinfo hardcoded directory fixed too – Windows will not allow you to run & autoelevate anything except legit InetMgr.exe from system32\inetsrv directory.
Bypasses alot of the methods used by UACme that is posted in my ::Wiki::
by admin
Thursday, March 10th, 2016 at 3:00 pm
CVE-2016-3115
Affected configurations: All versions of OpenSSH prior to 7.2p2 with X11Forwarding enabled.
Vulnerability: Missing sanitisation of untrusted input allows an authenticated user who is able to request X11 forwarding to inject commands to xauth(1).
Injection of xauth commands grants the ability to read arbitrary files under the authenticated user’s privilege, Other xauth commands allow limited information leakage, file overwrite, port probing and generally expose xauth(1), which was not written with a hostile user in mind, as an attack surface.
Mitigation / Workaround:
disable x11-forwarding: sshd_config set X11Forwarding no
disable x11-forwarding for specific user with forced-commands: no-x11-forwarding in authorized_keys
::More Info::
CVE-2016-3116
This also affects DropBear, from their Changelog:
“Validate X11 forwarding input. Could allow bypass of authorized_keys command= restrictions”
Mitigation / Workaround:
disable x11-forwarding: re-compile without x11 support: remove #define ENABLE_X11FWD in options.h
::More Info::
by admin
Sunday, February 7th, 2016 at 5:41 am
by admin
Monday, February 1st, 2016 at 3:40 pm
So I started working on a wiki to drop occasional oneliners and examples that I’ve come across that are useful. It’s a work in progress and any suggestions are welcome.
bhafsec.com/wiki/
by admin
Monday, February 1st, 2016 at 2:35 pm
The Sparkle Updater framework does not set HTTPS everywhere allowing remote command execution attacks. This attack will apparently work if allowing any app to run is set on OSX. Otherwise you get blocked by Quarantine and Gatekeeper, both prevent signed and unsigned applications from being automatically run without the user’s consent.
Src:https://www.evilsocket.net/2016/01/30/osx-mass-pwning-using-bettercap-and-the-sparkle-updater-vulnerability/
by admin
Friday, January 29th, 2016 at 11:39 pm
use-after-free flaw was found in the way the Linux kernel’s key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system. The vulnerability has existed since 2012. Here is a link to the full exploit which runs on kernel 3.18 64-bit, following is the output of running the full exploit which takes about 30 minutes to run on Intel Core i7-5500 CPU
github.com/PerceptionPointTeam





 Skype
Skype Email
Email Keybase.io
Keybase.io

