Who is the real mobman?
by admin
Thursday, December 13th, 2018 at 11:50 pm
So I have a bit of history with the old trojan scene from 20 years ago. I got my first computer in 1999 around that time I had also read articles in USA Today about BO2k being released at Defcon etc.. I had dialup Compuserve at the time , most of my friends that had online had AOL, so i used to try get free access on there and its where I learned to jack accounts from , at the time one of my friends suggested a program called Sub7. I used it on the regular, it’s where i learned how networking and how Window98 worked, I learned how file extensions worked, by changing the .exe to .com I could name the file something less conspicuous to trick the target into opening something called www.mypics.com. I learned programming because I had the need to make small 2kb webdownloaders in Microsoft Assembler (MASM) because targets wouldnt like to download a 300kb+ file over dialup.
So I was pretty well versed at the time on all the features and nuances of Sub7. I hung around IRC at the time with a bunch of smart people who still to this day I am very good friends with. I tried to keep track of a lot of people at that time and still have some people from time to time pop into the illmob IRC to say hi. My last remembrance of Sub7 back then was in 2003ish when the final version came out. The real mobman had released versions far and few between at that time and people wanted version that worked with XP (there was a hardcall to a dll that made sub7 fail and pop up a message box if you tried to get RAS passwords etc..) and other details I will get to later in this post. There was an attempt around 2009to reboot it with the ‘blessing’ of mobman by someone named read101. It was a shitshow I wrote about it in an article on here about it :::HERE::: it was basically a failed attempt to make it look like sub7 then used Nirsoft password recovery tools bound to the server.exe to do password recovery. A real shitshow. After that failed release it got quiet for a while.
I had gotten in trouble awhile back and was on probation, around 2010 FBI had paid me a visit asking a bunch of questions etc… they didn’t give me a reason for their visit but claimed they wanted help and that “it would benefit me i.e. money , equipment etc, done with probation…) but they never gave me reasons why they showed up or what they wanted to know. I had thought that becauseI filed a motion to be released from my probation early, (which I had also written over some IRC conversation help with Jeremy Hammond )
Eventually I blew them off. But curiosity got the best of me and I wanted to see if there was a Jeremy connection to the visit when he got busted for hacking Stratfor with LulzSec, I filed a Freedom Of Information Act (F.O.I.A.) on myself , after a number of years I got the results back (fucking F.B.I. and government are slow as fuck). So I got my results back eventually and found out at some point in 2009 there was an informant in Tennesee claiming that *I* was mobman and I had started coding newer versions of Sub7. I will provide screenshot if need be, the results I got back from feds were heavily redacted. That’s why they paid me a visit, They asked about botnets etc , I figured out later that they were working on taking down the CoreFlood botnet, which the agent that paid me a visit had took down along with help from Microsoft by seeing this article a few months later ::Article Here::
Flash forward to 2013, there was an article in ::Rolling Stone magazine::. It featured some ‘geek’ hackers one that stuck out was someone calling themselves ‘mobman’. So i’m like oh fuck he’s back, so i started to dox this new person “Greg Hanis”. Firing up Evernote I just started pasted odds and ends etc about him , found his Skype and started messaging him.The whole point of this article is not to shit on him as a person, but to shed light on this grift he has of being mobman. So as I was talking to him, I would ask him particulars of that era, nicks and handles of people in the IRC that I still recall, he kinda of shrugged them off when I was chatting saying he didn’t recall. I chalked it up to a decade of memory lost and also shrugged it off. I kept digging too though. I found arrests in Florida from online mugshot sites, found his social media profiles. I started digging but kinda of lost interest because There was people I knew that knew him personally from the scene. Eventually I think it was Defcon 2015 I had met him in person. I brought him to the room I was staying at with a friend , who had also know the real mobman from IRC, he even fired off some questions that Greg shrugged off. This went on for a few times at Defcon that I hung out with him. Didn’t question that he knew John Mcafee working with the failed venture DemonSaw, the time I snuck into the private party section of Hustler’s Club and drank all John’s liquor while I chatted up his wife Janice, getting drunker and drunker. (also which Greg said he could get us into as VIPs but I ended up sneaking by bouncers myself)
I started gathering more doxx over the years too, when I started getting into password breached database dumps. Now Greg, had always used the handle GregTampa for his online persona, why would someone go from a mysterious handle like mobman to a handle that exposes his name and where he was from. A lot of his cross-referenced emails and passwords popped up in the databases, none leading to anything sub7 related. The Wikipedia Article on Sub7 didn’t start mentioning Greg until after 2014.
Recently I had a pentest in Philadelphia this summer , close to where an old IRC friend lived. During the course of reminiscing we had talked about Sub7 and our memories of it. We also talked about Greg as mobman. I had mention he was weird and always was evasive when answering questions, we said we should confront him about it sometime. Then there was a Podcast that came out called Darknet Diaries in August of this year. Whenever Greg was asked about Sub7 he would use the same tactics of jumping around the questions, he sounded more like a user of Sub7 than someone who actually coded it. I talked with friend about it and he came to the same conclusion. We talked more about confronting him but never got around to it. Then The Many Hats Club did a podcast on him this past week. Same fucking shit, I’ll break down some highlights. Claims he was a teenager when he wrote it, to “hack people on Ultima Online” now going by his slideshare info seen here,
he says he was 15. Greg was born 10/27/1980 that would have been 1995. First off trojans werent really a thing yet, secondly Ultima Online wasnt released until September 1997, and third sub7 1.0 wasnt released until 1999.
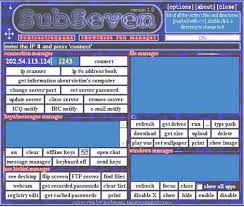
The Romanian Angle
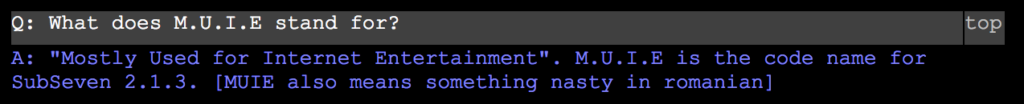
OK this is where we start to get into the juicy proof. My memory of mobman was always some euro guy , because not only did he speak like english wasn’t his first language, I had other friends that talked to him in Romanian on IRC. Secondly mobman gives shoutouts and dedication to B.U.G. Mafia in a release of Sub7, (they were an underground Romanian rap group). Another version on Sub7 was called M.U.I.E in which on the Sub7 site he said this:
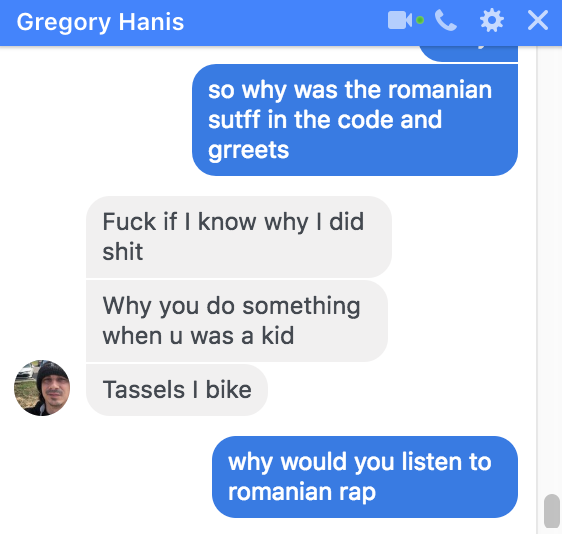
Greg is of greek heritage, which he admitted in chatlogs in which me and some friends started interrogating him in a Facebook group chat. In these same chatlogs inquire why would he give shoutouts to Romanian rap group, his only explanation was this:
Sub7 Details
In these same chatlogs , which I will link to, I start pressing on him some hardcore questions, of people in the scene back then, and particulars of the program itself. One of the first items is HardDrive Killer Pro, which was an old batchfile from someone named Munga Bunga, it’s intent was to recursively erase files on Win98 and 95 , rendering it useless if rebooted. mobman had bound this batfile to the server , because “one particularly lucky son-of-a-bitch named Sean Hamilton, ICQ #7889118. If Sean or someone with his ICQ account information stored on his/her computer managed to get the virus on their computer, the virus would proceed to erase the computer’s entire hard drive using Hard Drive Killer Pro. This also means that if you are running a computer infected with SubSeven and happen to add information to the registry that lists possession of ICQ UIN #7789118, it will instantly bomb your hard drive” Which was found out and used by people to wreck their victims. Greg’s explanation was in this chatlog: mobman1.pdf in which he claims a woman was his target.
Another issue was the master password. at some point it was either leaked or someone reversed the code to the server to find that was a backdoor password to control servers. Anyone could connect to it with the client and type the password of “14438136782715101980” and gain access to the victim. Greg was asked his explanation of the master password:
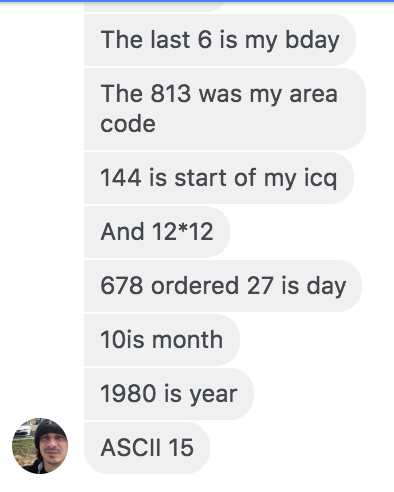
which might seem like a plausible answer had he not taken almost 2 hours to come up with. With that jumbled amount of numbers anyone could have lucked out , but he also faults, his ICQ number for gregtampa is 14204407 which can be seen in this old angelfire account , not 144 as he claims.

and the fact that the real mobman’s ICQ was 14438136 as seen ::here:: which makes up the first part of the master password….
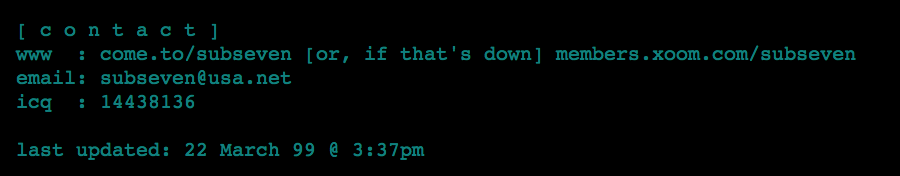
Also there was a time mobman posted that his leave of absence was due to moving to Mtl (Montreal) as seen here http://archive.li/KugEw
” [ guess who’s back… back again ]it’s been a while… i just recently moved to mtl, and as a result i’ve got more free time on my hands. sub7 is back.[ 10/27/03 5:25 am by mobman ]”
Besides living in Florida either with his mom or homeless, and more recently Alabama, he’s probably never been out of country , much less Canada to live. Also on The Many Hats podcast @ minute 1:59:44 he says he has a passport and has never been out of the country.
If you look at his github, has nothing coded in Delphi just PHP, granted Greg may know some thing, after all he graduated from ITT Tech, I found the proof he sent to The Many Hats Club. It’s password protected https://www.dropbox.com/s/mwerljtvfkh6vox/sub7-master-suite.zip?dl=0 in which I cracked, the password being : mobman
I still havent cracked some of the other password protected files in it yet
It’s a fucking collection of just the Sub7 binaries , no source code, no proofs, I even think I saw this posted on an old hack forum a while back.
Ill probably have more to add as i’m just starting , but If he has in any way proof anything that he is the indisputable author of Sub7 i’ll eat my hat. If anyone has any more information to add email me illwill at illmob.org
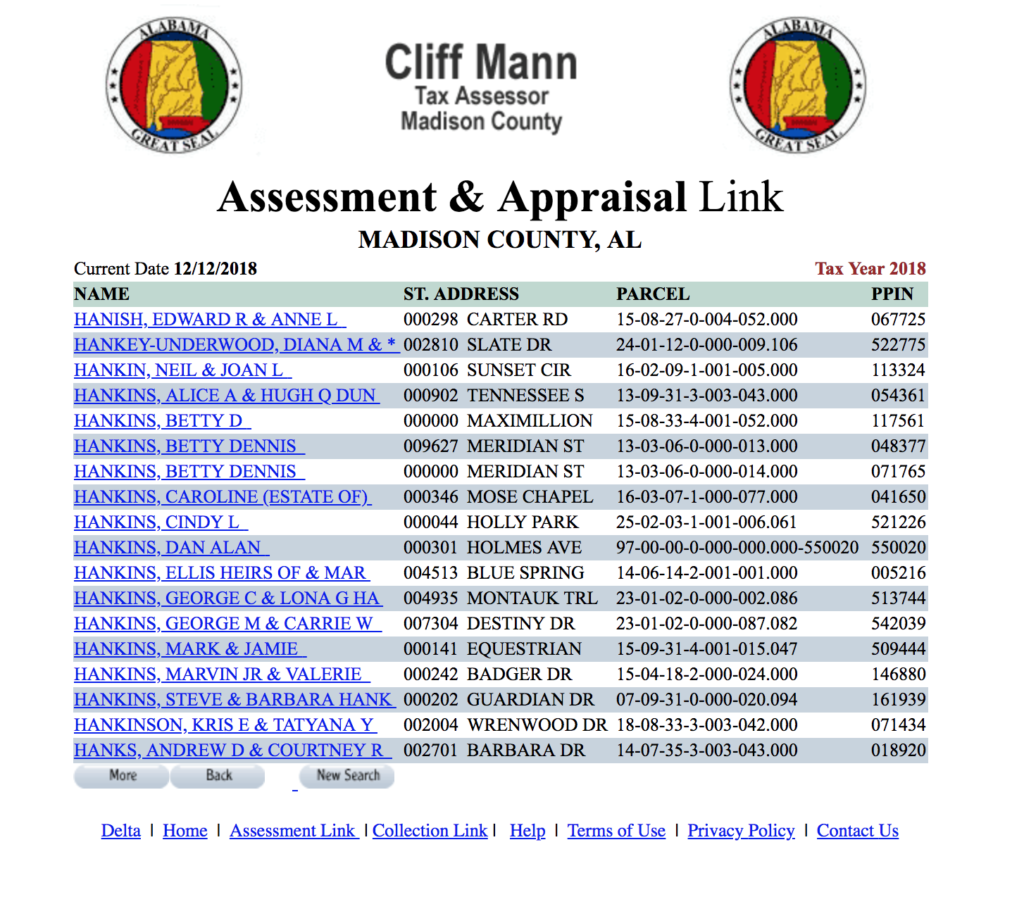
also he claims that he was made rich from selling his software to John Mcafee and working under MGT in the many hats podcast, I don’t see any land owned in Alabama by him


 Skype
Skype Email
Email Keybase.io
Keybase.io

